The world that has never been connected in the past few decades is being transformed into a permanently interconnected environment. The higher the degree of interconnection and interconnection, the more stringent the requirements for the corresponding safety regulations and standardized frameworks are. Because of this, the Continental Group places network security at the heart of product and service development. Technology company Continental Group is currently working on developing an end-to-end solution to ensure that the highest level of security is always maintained. Andreas Wolf, head of the Continental Group's body and safety business unit, explains: "To date, most intrusion reports have come from security researchers or "white hat" hackers. To ensure safety, from the first day of product development Network security should be considered as a top priority, and security holes should be eliminated from the source.†Comprehensive Protection: End-to-End Security Solutions To ensure a reliable safety system for complex automotive systems and components, Continental has adopted a multi-level approach to maintain a high level of safety. This program requires detailed risk analysis of new projects to ensure that products and services meet safety-related regulations. Wolf explained: "We call this process 'security and privacy threat analysis, risk assessment and risk management'. We are not only considering security issues in the early stages of development, but the security of the entire product life cycle." In addition, the main purpose of adopting an end-to-end security solution is to detect and prevent attacks against vehicles (external interface protection and monitoring). To this end, the Continental Group has taken protective measures against the communication interface between vehicles and the outside world. The automotive system itself also needs to be protected. A common method is to continuously check the communication abnormality on the CAN bus and encrypt the communication between the control units (vehicle network protection and monitoring). With regard to safety and security, one of the major measures considered by the Continental Group is the long-term monitoring of the status quo of automotive systems (vehicle health monitoring system). The results of the monitoring must be reported regularly to the Security Operations Center, such as the Security Operations Center operated by the Continental Group, in order to verify the safety of the vehicle fleet. Once serious problems are encountered, car manufacturers and suppliers can find solutions in a short period of time, develop security patches, and quickly update the fleet system through wireless updates. People do not have to go to the auto repair shop for help. Wolf said: "We are building a complete ecosystem of security factors to provide our customers with a customized design through a single channel, allowing customers to use these designs from the early stages of project definition." In terms of overall packaging, China The software products of Elektrobit Group, a subsidiary of the group, have been invaluable. When building an electronic control unit security architecture, developers can call basic software components and application software to secure the system. Four aspects of cyber security Safeguarding the network security of connected cars in the future is one of the major tasks for the entire automotive industry. The Continental Group looks at security issues from four perspectives. The first is the security of electronic components. Electronic components are equivalent to microcomputers and control various functional components in the vehicle, including engine control units, windshield wipers, vehicle entry control systems, and so on. The second is the communication security between the various components, which is related to the entire system of the vehicle. The third is the security of numerous interfaces between the vehicle and the outside world. Fourth, because cars have become part of the Internet of Things, when considering cyber security, they must jump out of the car's framework and extend to the cloud and back-end. "As we all know, absolute security is impossible to achieve. The battle between the auto industry and cybercriminals will never stop. However, our solution will set the most cutting-edge technical barriers to cyber attacks and maximize the protection capabilities. ." Toothless Crossed Roller Slewing Bearings,Three-row roller slewing bearings,Six Row Cylindrical Roller Slewing Bearings Huatao Group Limited , https://www.rollerandreducer.com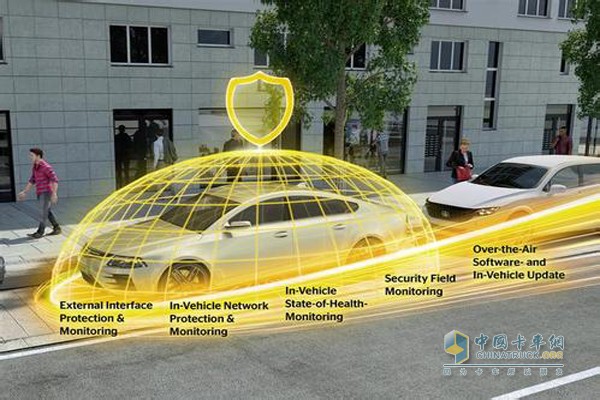 Continental Corporation escorts the safety of connected cars
Continental Corporation escorts the safety of connected cars
The realization of the latest infotainment functions in the future cockpit, safer driving experience, and smoother traffic are all due to the development of smart control and seamless connection of mobile services online. Full connectivity technology has brought us unlimited possibilities and is at the core of self-driving cars. However, some new features, such as the wireless update of on-board electronic systems, are also accompanied by risks.
Slewing Bearings, also known as slewing rings or turntable bearings, are rotational rolling-element bearings that are designed to support heavy loads and facilitate smooth rotation. They are commonly used in various applications where there is a need for rotational movement, such as cranes, wind turbines, excavators, and industrial machinery.
Types of Slewing Bearings:
Single Row Ball Slewing Bearings
Double Row Ball Slewing Bearings
Cross Roller Slewing Bearings
Three Row Roller Slewing Bearings
Applications of Slewing Bearings:
Cranes
Wind Turbines
Excavators
Industrial Machinery