Stainless Steel Sheet,Stainless Steel Coil,Stainless Steel Tube,Stainless Steel Pipe,Stainless Steel Shandong Rizhaoxin Metal Products Co., Ltd. , https://www.cysteelcoil.com

IoT security is a full-stack behavior. It is a subject of "communication, use, cloud, management, edge, and end". The whole ecological and unified cooperation and joint defense can only take effect. The strategy of strictly guarding against the Internet of Things is not able to penetrate. APT attacks to all corners. Therefore, we can comprehensively examine the countermeasures of IoT security from the aspects of IoT device startup, rootkit injection protection, DDOS attack defense, device security access, data and protocol security. In addition, the infrastructure of the IoT management platform, cloud platform, interconnection interface, and IoT business system must be secured.
1. Secure boot technology based on trusted computing
Trusted Computing is a secure computing technology promoted and developed by TCG (Trusted Computing Group). It is widely used in the field of computing and communication to implement a trusted computing platform based on hardware security modules to improve the security of the entire system and application software. Sex and integrity. As an emerging technology, its main objectives include the integrity of the computing platform, remote proof of the platform, security of data storage, and digital intellectual property protection.
As an advanced sustainable threat (APT), if it is not lurking in the deepest layer of the system, if it is not loaded before the operating system, if you can not balance the protection software in the startup process to achieve "self-kill", then I am really embarrassed to call myself "Qualified APT". The only way to be so arrogant is to control the system's operating rights. Trusted computing technology is the "Dinghai Shenzhen" in this "operational war". It uses layer-by-layer metrics to verify the integrity and correctness of each startup step, and ensures the integrity of the computing platform through the conductivity of the trust chain. Sex.
The metric is measured hierarchically from the bottom to the top. Usually, the software and hardware code (such as the security chip) that is started first is used as the root of trust, and the software and hardware started by the latter level are measured as the standard. The chain is passed backwards to ensure that the computing environment of the system is credible. The whole process follows the strategy of “measure first and then executeâ€. For example, when the Windows system starts, you can use a certain piece of code in the BIOS as the core trust root module (trusted root), BIOS/UEFI, WinLoader, operation on the boot chain. System image files, etc. are statically measured step by step (as shown in Figure 1).
Figure 1 The chain of trust initiated by the operating system
The trusted root must be trusted as the bottom of the entire system trust chain. Therefore, the trusted root is generally implemented by the manufacturer directly embedding the algorithm and the key in the security chip, and is not coverable. Therefore, this part of the code is also called Trusted Software Base (TSB).
As a veteran processing platform vendor, ARM has also proposed TrustZone technology for the security and trusted computing of consumer IoT devices. The technology is essentially a hardware platform structure and security framework, which divides the software and hardware resources of the system-on-chip into the secure world and the non-secure world (similar to the 0 ring and the 3 ring under the X86 system), which is ensured by the difference of access rights. Resource security, non-secure world and secure world communication need to be converted through the intermediate Monitor Mode (as shown in Figure 2).
Figure 2 TrustZone architecture view
Â
2. Rootkit defense technology
Rootkits are a common topic in the field of system security. No matter which processor architecture is used, no matter what operating system, rootkits are accompanied by ghosts. The so-called rootkit is the malicious code in the system for the purpose of hiding itself, controlling devices and obtaining private information. The “Internet of Things†is a rootkit malicious process/code module featuring information and control devices, so the defense against rootkits is particularly important.
The execution characteristics of the rootkit are as follows:
(1) Place the malicious code in the data area of ​​the memory, and execute the code in the data area by means of stack overflow or the like.
(2) The malicious code module is loaded into the application process by means of remote threading, default loading, etc., that is, "module injection".
(3) Obtain the data that you are craving by hooking up important methods of the operating system (such as system calls or interrupt response routines, etc.).
(4) Pass the filter-driven network protocol stack to obtain important network traffic and tamper with the data packet.
(5) Change the process execution flow by hooking the EAT/IAT (Export/Import Address Table) of the important executable module.
From the above operating characteristics of the rootkit, the means of preventing against the rootkit attack can be derived in reverse. Windows systems are in the forefront of defending against rootkits. Because Windows operating systems and computing resources are relatively loose, there are more mechanisms and means to ensure security. For the Internet of Things system, due to limitations in power consumption, computing resources, etc., the operating system is generally relatively streamlined, so it is even more necessary to develop a rootkit defense mechanism in a targeted manner.
(1) The IoT device communication module is short and precise, and there is generally no agreement stack. Therefore, the way of intercepting network packets through the filter driver does not exist in the IoT device.
(2) The IoT system does not have complex application mechanisms such as remote threads and default loading, so there is no need to consider module injection.
(3) Stack overflow is more common in IoT systems, so a data execution protection (DEP) mechanism like Win7 can be used to prevent malicious code from being executed in the memory data area.
(4) IoT systems also have important methods such as interrupt response routines, system call service routines, etc., and it is still necessary to prevent these important parts from being hooked. A Windows-like PatchGuard mechanism can be used to prevent these important parts from being overwritten.
(5) The kernel process signature verification mechanism can be used to block the installation and operation of unknown processes.
3. Anti-DDOS attack technology
DDOS attacks are also an unchanging topic in the field of network security. Regardless of the Internet of Things or the Internet, as long as it also supports the TCPIP protocol, it is in danger of being attacked by DDOS. DDOS is a type of attack. The core idea is that the target system is exhausted by the wheel war and cannot run other processes. It includes multiple attacks of subdivision. The common ones are as follows:
(1) SYN Flood
By forging a large number of non-existent IP addresses, the SYN packet is continuously sent to the server in a very short time, the server replies with the confirmation packet SYN/ACK, and waits for a confirmation reply that the client will never respond. In this way, the server needs to continuously resend the SYN/ACK until timeout. These forged SYN packets will occupy the unconnected queue for a long time, and the normal SYN request is discarded, causing the target system to run slowly or even ambiguously. This is a "wheel battle" made using the TCP transmission feature.
(2) ICMP Flood
The ICMP response is continuously requested from the target host in a very short time, resulting in the target system being overburdened and unable to handle normal IO services. This is a "wheel battle" made using the ICMP protocol.
(3) UDP Flood
A large number of UDP packets are sent to the target host in a very short period of time, causing the target system to be overburdened and unable to process normal IO services. This is a "wheel battle" made using the UDP protocol.
(4) ARP Flood
An attacker can send a large number of ARP request packets in a very short time to block normal network bandwidth, so that limited network resources in the local area network are occupied by useless broadcast information and cause network congestion. This is a "car battle" made with the ARP package, and the embarrassing is the bearer network.
In addition to the above-mentioned DDOS attacks created by the Layer 2, Layer 3 protocol, the application layer and the session layer protocol can also create the effect of DDOS attacks, such as crashing the WEB server through a short time of a large number of HTTP requests, and passing the super in a short time. A large number of streaming media session protocols have caused the video server to crash, etc. These attacks have catered to the original intention of the DDOS attack, that is, the extreme pressure causes it to cope with and crash.
Under normal circumstances, the defense of DDOS attacks is through the method of drainage, that is, the protection system is first required to determine that a DDOS attack has occurred, and then the traffic drainage mechanism is started, and the DDOS attack package is directed to the attack buffer area for digestion. Due to the large number of devices in the Internet of Things, it is especially important to guard against DDOS attacks.
(1) In the IPv4 environment, the private network is used to communicate with the external system. Due to the unidirectional nature of the private network penetration communication, the possibility of the external system actively launching a DDOS attack is low. Especially when the symmetric NAT service is deployed, the restriction from the external to the internal communication is very strict, and can also be to some extent. Block the DDOS attack stream.
(2) There may also be network isolation devices between the Internet of Things and the Internet, such as a secure access platform or a gatekeeper, whose security level can be set autonomously. Although its communication efficiency is low, it can perform deep detection (DPI) on network packets, and it can also impede DDOS attack flow to a certain extent.
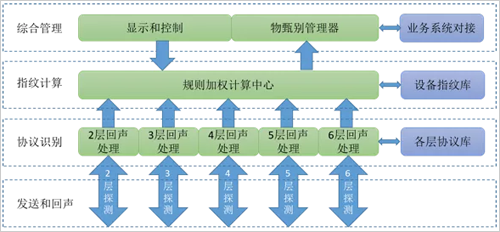
4. Internet of Things device fingerprint technology
Device fingerprinting is an emerging access access technology for IoT devices in recent years. The core principle is to generate a series of fixed and private information related to each device through the operating system, vendor ID, MAC address, port number, IP address, protocol packet type and other attributes of the device to achieve uniqueness of the device. . The Internet of Things platform identifies devices through the device fingerprint database, and can block and alarm devices in the non-fingerprint library. The traditional way to identify a device uniquely is through ID, but there is considerable shamability and replaceability in this way, and because the device ID is generally at the top of the OSI protocol stack, the counterfeit threshold is lower. The uniqueness of the device by device fingerprinting has a low degree of counterfeiting and substitutability.
(1) The operating system of the device will carry certain identifiers, such as version number, vendor ID, etc., the counterfeiting of these attributes is not easy, and the kernel state variables may be changed by means of a patch.
(2) Attributes such as MAC address, IP address, and port number have uniqueness of the device. Although they are also counterfeit, it is not easy to spoof these combined attributes.
(3) Although the protocol packets follow certain standards, the headers or packets of the device protocol of each vendor may have some private information. For example, the User-Agent attribute in the SIP protocol header field is accompanied by the vendor information. For example, the more subtle differences between the time interval of the protocol interaction and the reply characteristics are also important components of the device fingerprint.
Therefore, the uniqueness of the device by the device fingerprint, the detection device online, the device private connection, and the device counterfeiting have high non-fogability and irreplaceability.
Device fingerprint generation includes active detection and passive monitoring.
(1) The main idea of ​​the active detection mode is to actively send ICMP, UDP packets to the IOT device, or actively establish a TCP connection, and even initiate some protocols above the application layer to detect the device's reply information (such as ICMP echo reply, ICMP port). Unreachable, HTTP Response and other messages), based on these messages to identify the special attributes of the device. Some manufacturers will also support some private protocols specifically for identifying the non-foginess of devices.
(2) The main idea of ​​the passive listening mode is to listen to the interactive packets of the device through the network probe, and bypass these packets to the collection end for analysis, and determine the source port, source address, MAC information, and packet characteristics. The non-replaceability of the device.
Figure 3 An object discrimination system based on the OSI protocol stack fingerprint echo
Device fingerprints have been widely used in the field of video surveillance. However, in other areas of the Internet of Things, due to the complexity of protocol types and many devices are not in the TCPIP network, there are not many application scenarios.
5. Data Security Technology
IoT data security includes the two connotations of data security and protocol security. But no matter what kind of connotation, its essence is the encryption and decryption of data and protocol messages, and of course the certificate certification mechanism of the agreement. In the security field, the Ministry of Public Security has already developed the GB35114 standard, and divided the ABC three levels according to the level of confidentiality, respectively, authentication and encryption of protocol messages, authentication of video NALs, and encryption and decryption of video content itself.
The banning of national mandatory standards is a footnote to data security. (Author: Tan Shenzhen Li-wei-chi Technology Co., Ltd.)